Configure Forms Based Authentication with Active Directory Membership Provider
In SharePoint 2010 for a
web application we can enable both windows,
forms authentication. In earlier implementation to do this, we have to
create two web applications which has different zones and different
authentication. But, with the new claims based authentication a single
application can have the capability to configure both windows and forms under
single URL. All this is possible because of the authentication framework is
built on Microsoft Identify Foundation. Below steps describes the
implementation of FBA with Active Directory Membership Provider in
SharePoint 2010.
- Create a new web application with Claims Based authentication enabled.
- Adding Configuration information to web.config in Central admin, our new web app, and in the STS web service
- Add a User Policy to our web app that will grant an FBA user rights to the site
- Login to the site and check.
Create a New Web Application
To Start-with, Open Central Administration web site and Navigate to Manage Web Applications, and then click on the new button in the ribbon to create a new web application.
In the Authentication mode, select Claims Based Authentication.
Once we select the authentication mode to be claims, Windows Authentication is also plugged in as one of the provider in Identity Providers. Check the “Enable Windows Authentication” check box if you’d like Windows Authentication ALSO enabled for this web application.
We can also choose to enable ASP.NET Membership and Role Provider here. In this case, we’ll need to provide the corresponding provider names in the text boxes. The web.config file entries can be added later.
Once you fill the other details click Ok to create a new web application and also create a top level site collection.
Adding Configuration
information to web.config
Basically we need
to modify 3 web.config files for enabling claims:
- The config file of the Central Administration site.
- The config file of the Web Application.
- The config file of the STS (SecurityTokenService) Application.
This is important because it is this service that will ensure claims
tokens are being passed correctly between the provider (in our case AD)
and the consumer (CA and our Web Application).
- Open the web.config of Central Administration and add the following entries.
Connection
String: Make sure the below marked line (in yellow) to change as per
your domain name.
<connectionStrings>
</connectionStrings>
Provider
Entry:
<membership defaultProvider="ADMembers">
<providers>
<add name="ADMembers" type="System.Web.Security.ActiveDirectoryMembershipProvider,
System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" connectionStringName="ADConnection" enableSearchMethods="true" attributeMapUsername="sAMAccountname" />
</providers>
</membership>
People Picker Entry:
People Picker Entry:
Add the below line between <PeoplePickerWildcards></PeoplePickerWildcards>
for the People picker to include the FBA users in the search results.
<add key="ADmembers"value="*" />
Note: The
connection string element should be present outside of the
<system.web></system.web> section and the provider element should
be present within <system.web></system.web> section of the
web.config file.
- Open the web.config of newly created WebApplication and add the following entries
Connection
String:
<connectionStrings>
</connectionStrings>
Provider
Entry: Add this entry below the default entry which will be already exist
under membership provider
<add name="ADMembers" type="System.Web.Security.ActiveDirectoryMembershipProvider,
System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" connectionStringName="ADConnection" enableSearchMethods="true" attributeMapUsername="sAMAccountname" />
After adding It should be something like below snippet.
<membership defaultProvider="i">
<membership defaultProvider="i">
<providers>
<add name="i" type="Microsoft.SharePoint.Administration.Claims.SPClaimsAuthMembershipProvider,
Microsoft.SharePoint, Version=14.0.0.0, Culture=neutral,
PublicKeyToken=71e9bce111e9429c" />
<add name="ADMembers" type="System.Web.Security.ActiveDirectoryMembershipProvider,
System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" connectionStringName="ADConnection" enableSearchMethods="true" attributeMapUsername="sAMAccountname" />
</providers>
</membership>
People Picker Entry:
Add the below line between <PeoplePickerWildcards></PeoplePickerWildcards>for the People picker to include the FBA users in the search results.
<add key="ADmembers"value="*" />
·
Open the web.config of STS
web service and add the following entries, to find the web.config Open IIS
and navigate SecurityTokenServiceApplication
and click Explore in the Right pane.
Connection
String:
<connectionStrings>
</connectionStrings>
Provider
Entry:
<system.web>
<membership defaultProvider="ADMembers">
<providers>
<add name="ADMembers" type="System.Web.Security.ActiveDirectoryMembershipProvider,
System.Web, Version=2.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" connectionStringName="ADConnection" enableSearchMethods="true" attributeMapUsername="sAMAccountname" />
</providers>
</membership>
</system.web>
After doing all these configuration
changes do an iisreset to make the
changes effective.
Grant permissions to FBA
Users.
To Specify the Provider name in the
Web application, open Central
Administration site, Navigate to “Manage
all web applications” and select the respective Web application and click
on the Authentication Providers from
the ribbon and select the Zone from the popup.
Specify the Provider name and save the changes. Now to grant permissions to FBA
Users select on the Web application
in central administration and click on the User
Policy from the ribbon.
2. Select the respective Zone to which the User needs to be added or
select ALL zones and click Next.
3. Here you can see the difference in the Select people and groups
dialog box, where you various section in the left pane. And now if you search
for a User, you can find 2 results for the same user. Select the FBA user from
the result and add to the site.
4.
Select the respective permissions for the User and click Finish.
5.
Now you can check the Claim Identity name of the new User here.
We can check here how the claims in getting framed; match this
with the above Identity for clear understanding.
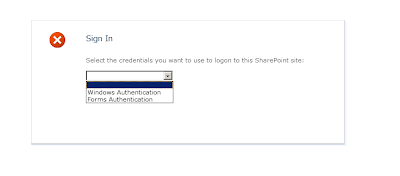
Login to the site:
Now the site is ready to login with Claims based authentication. Navigate
to the newly created site collection which then redirects to the default Login screen, where user can
choose between Windows Authentication
and Forms Authentication.
- If we choose Windows authentication, default windows credentials will be used for logging into the site.
- If we choose Forms authentication, user will be prompted for the Credentials.
Select Forms Authentication and it will redirect Forms login
screen, then provide the user
credentials of the User which we added earlier in User policy.
Now the SharePoint 2010
site is successfully configured with Forms
Based Authentication using Active directory membership provider.













No comments:
Post a Comment